I have often heard business owners and CISOs state that they are not a target of nation-state actors or that they are outside the ballpark of such sophisticated attacks, and I cannot help but cringe. State-based actors operate very similarly to cybercriminals. The only difference is that they have their governments’ backing, support and finances.
Nation-state actors have partaken in espionage, malware, ransomware and straight-out data destruction. Like most cyber threats, they will cast a net to see who bites. Yes, in some instances, specific organisations will be targeted. Still, the funding for these exercises must come from somewhere, and it is generally coming from everyday cyberattacks that we hear about in the news or from distraught family members. (Did you know that cybercrime affects individuals more than organisations? It makes sense; there are more people than companies out there, but these are targeted attacks against mums and dads, children and grandparents!)
Additionally, you have the knock-on effect of nation-sponsored cyberattacks. The US Stuxnet was designed for Iran’s nuclear plants; however, it got out into the wild and spread to 115 countries infecting between 90,000 to 100,000 systems globally. While NotPetya, created to target Ukraine, spread to 60 countries destroying the computer systems of thousands of multinational organisations.
What do we mean by nation-state actors?
Before I begin, a distinction must be made between nation-states and nation-state actors.
A nation-state is simply another word for the political unit, where the state and nation agree or are harmonised, defined as congruent.
In contrast, nation-state actors have a negative connotation and are defined as actors who aggressively and persistently target public and private sector networks for criminal or political gain.
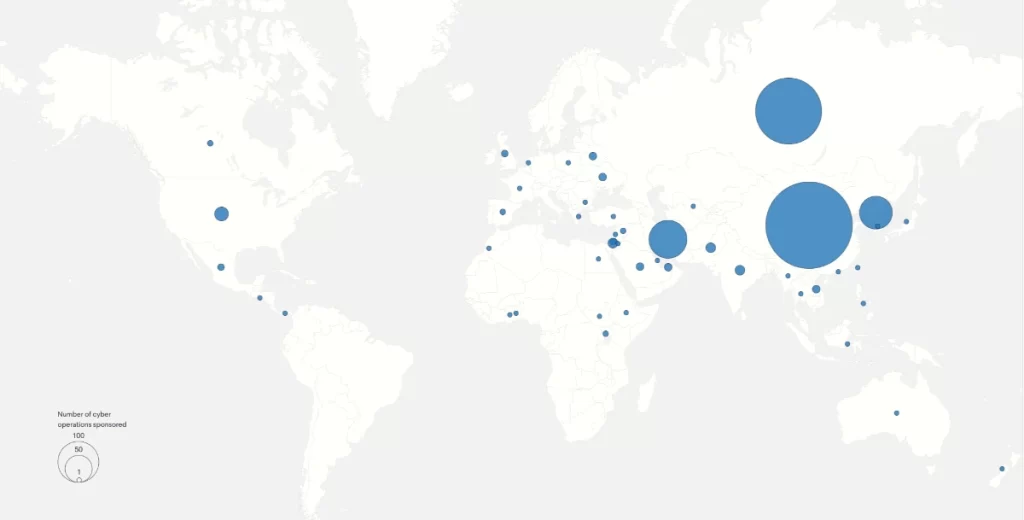
Without pointing fingers, the Council of Foreign Relations have in place a cyber operations tracker, a database of publicly known state-sponsored incidents since 2005 and placed the data on a map for our visual pleasure.
Source: https://www.cfr.org/cyber-operations/#Map
Ok, perhaps I am pointing fingers a little 😉
The page also provides a breakdown of attacks if you would like further information or examples of nation-state-backed cyber campaigns.
The major players
The map demonstrates that China, Russia, Iran and North Korea are the major players.
China
As our map above indicates, China has been the most active country since 2005 to undertake nation-state-backed cyber campaigns. In 2006, APT1 was one of the first state-backed cyber groups to emerge, with an estimated 141 victims of espionage across multiple industries since its establishment. In 2014 the FBI put out an indictment against members of APT1 and continued to indict members of Chinese hacker groups for various cybercrimes, for example, APT41 in 2019. One of the more fascinating indictments was against four members of the Chinese People’s Liberation Army who were indicted in 2020 for
“breaking into the computer systems of the credit-reporting agency Equifax, and for stealing the sensitive personal information of nearly half of all American citizens, and also Equifax’s hard-earned intellectual property”.
There are too many to choose from when researching recent cyber events accredited to China. Latest headlines include “China-backed hackers spying on US critical infrastructure”, “Chinese malware hitting Taiwan”, and reports of “a wave of cyber-attacks targeting US corporations”.
Russia
For those of you who know me, I have a deep fascination with state-sponsored cyber activity, having completed my PhD in Russian cyber warfare. However, what many people would not know is my decision to research and write on Russia came after learning the story regarding GameOverZeus (GOZ).
GOZ was a peer-to-peer botnet created by Evgeniy Mikhailovich Bogachev. In a thrilling write-up entitled Inside the Hunt for Russia’s Most Notorious Hacker, Garrett Graff describes the steps taken to discover and take down the botnet. If you have time, I recommend the read. What fascinated me was the aftermath of the takedown and what the FBI and cybersecurity experts discovered. The spread of GOZ was controlled through configuration files that told the malware where to spread based on IP ranges, ensuring the malware did not target Russian citizens. Further, the analysis of the files captured demonstrated that GOZ:
- had been tracking various geopolitical developments that affected Russia,
- had conducted keyword searches on English language documents with terms such as Top Secret and Department of Defence,
- had undertaken keyword searches on infected computers in Turkey for terms such as weapon delivery, arms deliver, Russian mercenary and Caucasian mercenary, and
- had undertaken searches to discover Georgia and Turkey’s foreign intelligence and ministry documents.
The Russian government, most likely the FSB, had seconded part of Bogachev’s botnet to spy on its neighbours. How fascinating is that!!!!!
There are several Russian advanced persistent threat groups I could write about. However, one of the most famous names associated with Russian state-sponsored attacks is APT28. Other names given to this group include Fancy Bear, Pawn Storm, Sofacy Group, Sednit, Tsar Team and Strontium. APT28 is associated with two Russian military agencies, 26165 (The Cyber Unit) and 74455 (GRU). APT28 has been operating since 2008 and is notorious for developing exploits, spear-phishing attacks and customised malware. I am also fascinated with this group after they successfully hacked into the Democratic National Committee in 2016 and wreaked havoc on Hillary Clinton’s campaign by leaking confidential documents. A more recent attack contributed to APT28 may be seen last month (May 2023) after they flooded Ukrainian government agencies with emails regarding bogus Windows updates.
Iran
In 2013 Hamid Firoozi, an Iranian hacker said to be part of the Islamic Revolutionary Guards Corp, broke into the command-and-control system of Bowman Avenue Dam in the US. Due to maintenance occurring on the system, the ability to release water was disabled. However, as this appears to be a one-off attack, it is most likely that the goal of the exercise was not to release water, merely to demonstrate that Iran had the power to mess with US infrastructure. Let’s be fair, anyone dealing with OT and SCADA devices back in 2013 will happily tell you that wreaking further havoc would not have been a tall order. The attack was said to be a response to Stuxnet, the 2010 worm reportedly destroying one-fifth of Iran’s nuclear centrifuges. In the same year, Iran established APT33 or Elfin, a cyber-espionage group backed by the Iranian government. Since then, other groups have been formed within Iran, but APT33 remains the most impressive. According to a Mandiant report, APT 33 has targeted organisations across multi industries and nations, including the US, Saudi Arabia and South Korea. Sticking with its original mandate of cyber-espionage, APT33 is believed to be targeting Saudi and South Korean petrochemical industries to gain a competitive advantage as it looks to expand into the petrochemical industry.
Interestingly, although APT33 is still widely written on, they do not seem very active currently, with their last spate of activity occurring during the height of COVID. However, Microsoft announced in May 2023 that Iran, in general, had been ‘rapidly accelerating’ cyberattacks since mid-2022. The Iranian group Mint Sandstorm have been found responsible for these attacks.
North Korea
One country that has received a lot of notoriety for cyber activity over recent years is North Korea. Part of this notoriety is off the back of a 2021 Indictment which spans 2014 to 2021. In 2014, Sony Pictures Entertainment was hacked in retaliation for ‘The Interview’, a movie that depicts the fictional assassination of the DPRK leader. According to reports at the time, Sony was held to ransom by a group calling themselves Guardians of Peace, stating that The Interview was an act of terrorism and that if Sony proceeded to show the film, they would release Sony’s unreleased films, plans for future films, scripts and other information. Sony, at first, was planning to release the movie as scheduled, but due to security concerns, it changed the release to only those independent cinemas that wished to show the film and online video demand platforms. What I found fascinating about this incident was the knock-on effect it had. Together with the new releases, the hackers also released a plethora of emails, including those from Amy Pascal, a movie executive and head of Sony, who retired from her position after racially insensitive emails sent by her to various people were released.
Other attacks over the years have included bank heists, ATM cash-out thefts, and ransomware, including the famous WannaCry. According to the latest news reports, North Korea is responsible for stealing three billion in cryptocurrency over the last five years through elaborate schemes, including posing as recruiters to gain sensitive information (to see how to protect yourself read this article). The US estimates that currently, North Korea has 6,000 people working within their cyber unit!
The United States
It would be negligent of me not to mention the US in all of this, especially as it appears that they were the first government to assemble a cybergroup. The Equation Group was formed as part of the US’s Tailored Access Operations (TAO) of the National Security Agency (NSA) in 1998. The group’s mission was to monitor and infiltrate enemies of the US, both foreign and domestic. In fact, in 2019, the Trump administration quickly reported to the New York Times that:
“the United States is stepping up digital incursions into Russia’s electric power grid in a warning to President Vladimir V. Putin and a demonstration of how the Trump administration is using new authorities to deploy cyber tools more aggressively.”
Another example of the US’s cyber capabilities may be seen in the exploit EternalBlue, which was developed and then lost by the NSA to hackers. EternalBlue would be used in the WannaCry ransomware attack (mentioned above) only one month after it was stolen.
What does all this mean?
Nation-state actors have been here for a long time and will continue wreaking havoc on businesses and individuals. Sometimes non-government bodies and individuals feel the aftermath of chaos directed at other countries, such as the example of NotPetya. Other times we will feel the knock-on effect of careless governments losing zero-day exploits to nefarious people, as per the case of the NSAs EternalBlue. And then other times, we are the target.
According to a 2022 Suisse Report, Australians have the highest median wealth in the world. Threat actors read, research, and then tailor their attacks to the audiences they want to target. Last year, Australia came in fourth with ransomware attacks globally, and this year we are coming in third place. This is not a good thing. We do not get a bronze medal, as if we have just participated in the Olympics. Instead, we hear nightmare after nightmare of family and friends being left destitute and organisations going bust. To add insult to injury, there is an excellent chance that the money or information stolen is being used to support the war in Ukraine or used to go towards North Korea’s missile program.
There is so much more I can write on the subject, but I will leave it here for now. If you take away anything from this article, I hope it is, anyone can be a target of a nation-state actor. Nation-state actors are generally more motivated and have more resources than cyber criminals, so we must keep our guard up and ensure that we live an online life of scepticism where we verify first and then trust.




0 Comments