Organisations cannot outsource their risk. Too often, I have gone into an organisation and inquired about certain controls, only to receive the answer, ‘Oh we use cloud services so do not have to worry about that’. News flash, YOU DO!!!! And the recently released ISO/IEC 27001:2022 and its new control ‘5.23 Information Security for Use of Cloud Services’ is reminding us of this fact.
There are many benefits to choosing cloud computing. According to Forbes, the benefits include:
- Better insights from big data, as all your data can now be saved in the one place.
- The cloud is flexible and scalable.
- Workers can now collaborate more efficiently.
- Business continuity and disaster recovery are usually tied in nicely with your cloud solution, and
- Cloud computing is cost-effective and (should be) simple.
What are the risks of cloud computing?
But there are also challenges with cloud computing, and this includes security and privacy risk. Some of these risks are summarised in a neat little video put together by CISCO to advertise their CloudLock Cloud Access Security Broker solution, entitled ‘Cloud Security: It’s Tuesday, Carl’. I know nothing about this solution so cannot comment on it, but the video is great:
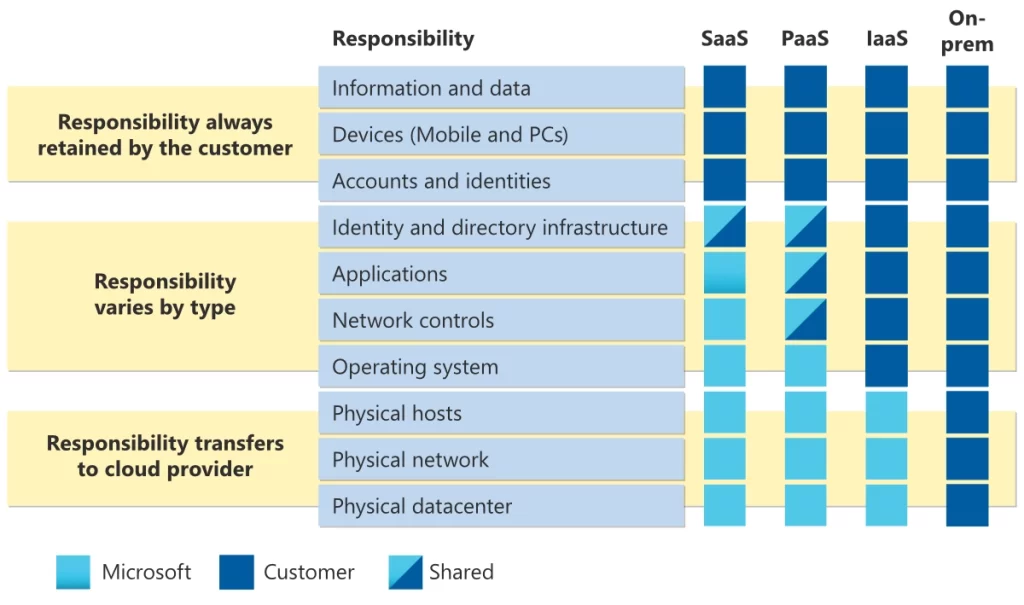
The good news, most cloud service providers will let you know upfront how the division of responsibility is broken up, between your cloud service provider and the customer. For example, Microsoft has put together this nifty matrix that is nice and clear and straight to the point (thanks to one of my students for reintroducing me to this matrix!).
What does ISO 27001 Annex A 5.23 say?
Going back to ISO/IEC 27001:2022 5.23, the control states:
“Processes for acquisition, use, management and exit from cloud services shall be established in accordance with the organization’s information security requirements.”
ISO 27002 cloud security implementation advice
In 27002:2022, this is extended to specific guidance on how an organisation may accomplish this.
First and foremost, the framework calls for a policy on cloud services. If your organisation has not yet had the conversation, you need to determine:
- whether you want to only use one provider, or you have the capacity to manage several
- whether you want your data to be held locally, or it is not a requirement (make sure your privacy policy reflects your decision on this)
- roles and responsibilities (this includes what your cloud provider will be responsible for and what your organisation will manage), and delving a little deeper
- whether the responsibility of cloud computing is left with IT or if each area manages their own cloud instances (I shudder at this thought, but each to their own!).
- Lastly, you need to determine your exit strategy when leaving a cloud provider, as remember the control requires you to put in place a process:
“for acquisition, use, management and exit from cloud services.”
The second part of developing a policy for cloud computing is ensuring that those who need to know about this policy, know about it. So, procurement, IT, and your project teams. It is up to your organisation on what this policy may state, but if you are already using a cloud solution, you may want to dictate that any future expansion into the cloud occur using your existing platform (excluding SaaS). If there are compatibility issues, then you will need to carry out an information security risk assessment to ensure any possible or known risks are captured.
This brings us to the second paragraph under ISO 27002:2022, ‘Guidance’. You need a process in place to:
“manage information security risks associated with the use of cloud services.”
I was extremely happy to read that ISO/IEC 27002:2022 allows for this to be an extension or part of an organisation’s existing approach to managing external parties, as that is exactly what a cloud provider is, an external party. Therefore, you will need to undertake the same type of assessment you would for any third party.
I know, I hear you. Most of the cloud suppliers on the market are large corporations who are not going to take the time to undertake your third-party risk assessment questionnaire, and nor do they need to. But you do need to do your due diligence, and examine SLAs, contracts and agreements to ensure that you understand the fine print. Before even commencing your engagement with a cloud provider, you should already have predefined questions that you will be looking to answer. A lot of these questions will be specific to cost, capacity, and management, but there should also be security questions in the mix. For example:
- What training is available to help upskill staff and educate them to ensure the configuration is performed securely?
- What does the cloud provider’s security program look like?
- Has the cloud provider been in any breaches, and if so, how did they respond?
- What are the compliance requirements of your organisation and does the cloud provider meet those requirements?
ISO 27002:2022 provides a whole list of provisions for the protection of your organisation’s data and the availability of services. I will not list them here, instead, you can read them on page 42 of the framework and I encourage you to read them. But going back to my original statement that you cannot outsource your risk, you need to be making sure that your cloud service provider is not outsourcing their risk either, so do your homework. You would hate to find out in two years’ time that the cloud provider you went for, due to the amazing price you received, is actually being backed by a questionable nation-state, who has back-doored the cloud solution and there is a good chance has been accessing your data since you signed-up!
How do I comply with ISO 27001:2022?
One of the things I love about ISO 27001 is it requires the user to take a risk-based approach, and under 5.23 you are being asked to define and communicate how it intends to manage information security risks associated with the use of cloud services.
The easy way to identify risks associated with a cloud service provider is to undertake a risk assessment at the start of the project and document the risks, the owners and action plans. Unless of course, you accept a risk, in which case, you only need the owner’s sign-off on that risk. For your reputable cloud service providers that have market share and have been around forever, this may be a box-ticking exercise, and I acknowledge this. But I am always surprised by what I discover when I follow a documented process around risk, and that is exactly what you need to manage your cloud providers, a documented process.
Realistically, nearly everything we use today in business is cloud-based, whether it is our CRM, accounting software, or prescribed storage space. It is all cloud and you need to perform your due diligence. You do not have to do risk assessments yearly. If your cloud provider is a low risk and you are satisfied, schedule a three-yearly review. Just make sure if changes are made that can impact your organisation, you push the review to the front of the list so you stay on top of your risks. You do not want to be caught out having a cloud solution as a low risk, only to have things change and overnight it becomes a critical risk when you were not paying attention. Speaking of managing your cloud and supplier risks, you will need a register to keep track of them, otherwise, you will get caught out!
The last thing I will say is to treat your cloud providers the same way you would treat any third-party provider. Undertake a risk assessment at the start of the cloud project, ensure each risk has a risk owner and do not let the risks drop off your radar. Make sure they have a due date.
One control which is the same for every organisation is staff awareness. You will need to ensure that staff are doing the right thing, so as not to expose your organisation. Just ask Carl!
A second control that you need to keep on top of is testing. Undertake yearly configuration reviews to ensure your cloud environment has been set up securely, functionality and service changes have been taken into account, and that any new security controls are turned on and configured correctly. I used to love performing configuration reviews when I was a Senior Consultant. We don’t provide configuration reviews at Morrisec, but if it is something you need, get in contact and we will put you onto someone who can help!
That is all I have, I can talk for hours on cloud security, and I might just do that in another article, but for now, I hope I have given you enough ammunition to start managing your cloud providers under ISO 27001:2022.
As always, if you need any help with ISO 27001:2022 or managing your third-party suppliers in general, including your cloud providers, we are here to help… queue the action hero music!




0 Comments