Business Email Compromise (BEC) is the impersonation of a trusted entity or individual to deceive employees, customers or business partners into taking some action that benefits the threat actor. We have all heard the term and we have all seen the continued rise in this type of attack over the last few years, but my description above only just scratches the surface.
One recent report analysing threat trends across 2022 saw a 356% growth in advanced phishing attacks, in addition to an 83% growth of BEC attacks. Gartner’s February 2023 Market Guide for Email Security report found:
“Impersonation and account takeover attacks via business email compromise (BEC) are increasing and causing direct financial loss, as users place too much trust in the identities associated with email, which is inherently vulnerable to deception and social engineering.”
In a lot of our articles and posts, we talk about the need to understand the threat actors that target your business. Armed with this knowledge you can understand their varying tactics, techniques and procedures (TTPs) allowing you to develop strategies to protect yourselves against these attacks. BEC attacks are evolving at a rapid rate and so to are threat actors’ TTPs. In this article, I’ll delve into BEC attacks and the lengths threat actors are taking to stay one step ahead, including the use of AI to advance their attacks. I will also talk about actions you can take to reduce your risk.
What is a business email compromise attack?
The first thing to discuss is the term business email compromise. The term itself could be construed that the compromise of a business email account is required, but this isn’t the case. While threat actors leveraging a compromised account is one tactic, having access to a legitimate account is not required to be classified as a business email compromise attack.
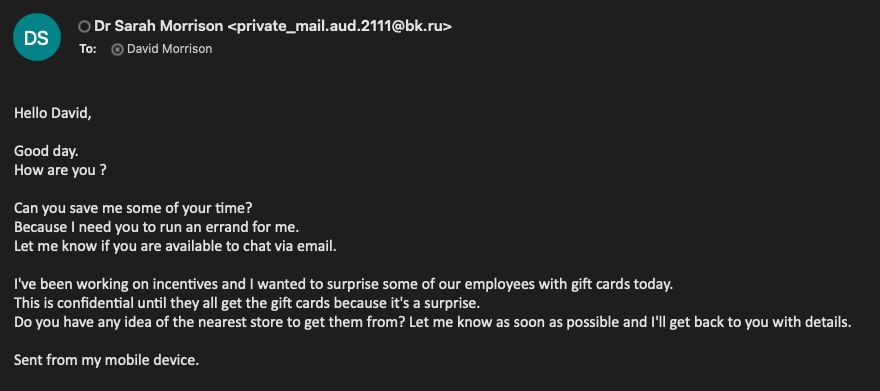
BEC scams commonly involve what is called email spoofing, where the threat actor forges the sender’s email address to make it appear as if it is coming from a trusted source within the organisation. This technique does not require access to the actual sender’s account. BEC scams performed with little effort by the threat actor will show the spoofed user’s name, but the email address it is coming from won’t match, making it easy to spot if you are looking. This is obvious in the BEC email I received from Dr Sarah Morrison recently and I have included it below. Ignoring the fact I know she wouldn’t be making this request via email, coupled with I know her writing style, I would definitely question why she is emailing me with a Russian email address 😂
The attack above is most likely automated, with details scraped from online then hundreds or thousands of emails sent out using the scattergun approach hoping someone will fall for it. It takes little to no effort by the threat actor but could lead to huge returns.
On the other hand, a threat actor that is actively targeting your organisation will register domains similar to yours, ones that at first glance you may not notice are incorrect. This is generally referred to as ‘typosquatting’. The term was originally used for a domain registered to be very similar to another domain, hoping that someone mistyping the domain in their browser would end up there. The term is now used for those domains that also lure victims through phishing or other scams.
When typosquatting, a threat actor that wants to spoof example.com may register exampIe.com, where the letter ‘l’ has been switched for a capital ‘i’. Depending on the font in the user’s email, this change may be very difficult to notice.
I talk about threat intelligence a lot as it is a critical part of an effective security strategy, and one area organisations should look at within their threat intelligence processes is monitoring for typosquatting domains. Being aware of a typosquatting domain can be a warning sign of an upcoming targeted attack.
What is the difference between BEC and Phishing?
So at this stage, you may be thinking BEC just sounds like phishing. So what’s the actual difference? While there is overlap between the two, BEC scams differ in their techniques, targets, overall objectives and often their sophistication as well. Let’s take a look at each of these.
Techniques
The main technique used by BEC attacks involves impersonating a trusted entity or individual through email spoofing or other social engineering techniques. This can go beyond the realm of phishing (email) and could include smishing (SMS messages) or vishing (voice/phone calls). The threat actor’s aim is to deceive employees, customers, or business partners into taking specific actions that benefit the threat actor, such as initiating an unauthorised wire transfer or disclosing sensitive information.
As they appear to be from a known individual, and are requesting the recipient to take some sort of (what appears to be) legitimate action, they don’t tend to contain malicious content, such as a malware-infected attachment or a link to a malicious website. They are purely text-based, your typical business-looking email, so they bypass traditional email solutions that look for malicious attachments and links.
Phishing, on the other hand, generally purports to be from a reputable source, such as a business, rather than a trusted person you know. Think of your typical AusPost or FedEx phishing emails that pretend to be that company and try to drive you to a fraudulent website, open a malicious attachment, or download a malware-infected file.
Targets
Standard phishing attacks, ignoring spear-phishing and whaling for now, target a large number of potential victims. These could be targeted at business or personal email addresses. The threat actors cast a wider net by sending mass emails or messages to lots of recipients hoping to get a bite. As with the example above, they often impersonate well-known companies, financial institutions, or online services, aiming to trick recipients into revealing their personal information or login credentials.
BEC attacks primarily target specific individuals within an organisation, personnel with access to financial resources or sensitive information. The threat actors often focus on executives, executive assistants, employees responsible for financial transactions, or individuals involved in procurement or supplier relationships. These attacks are far more targeted and the target may only be one individual within a company.
While we are on the topic of targets, business email compromise attacks are industry agnostic. When looking at some of the top threat actors using this attack vector, target multiple industries simultaneously, including manufacturing, financial services, technology, retail, healthcare, energy, and media.
Objectives
The primary objective of BEC attacks is to gain a financial reward, or to gain access to sensitive information, often to then launch further more targeted attacks. Threat actors may attempt to fraudulently obtain money, divert payments, or extract valuable data from the target organisation.
Phishing is more targeted around gaining access to information, such as login credentials, credit card details or personally identifiable information (PII). The stolen information can then be used for various purposes, including identity theft, financial fraud, or gaining unauthorised access to accounts or systems. Phishing leads to further attacks whereas BEC attacks often aim to gain access to money directly from the attack.
Sophistication
BEC attacks often involve a higher level of sophistication and customisation. Threat actors carefully study their targets, monitor communication patterns, and employ social engineering tactics tailored to specific individuals or the target organisation. They may invest significant effort into creating convincing spoofed emails or manipulating employees through persuasive techniques.
Phishing attacks can range from simple and generic to more sophisticated campaigns. While some phishing attempts can be relatively straightforward, others may involve advanced tactics such as spear phishing, where threat actors personalise their messages by using information obtained from other sources, making the emails appear more legitimate and increasing the chances of success.
Advanced BEC scams
We have all seen or heard about your common BEC scams, such as the screenshot earlier where the threat actor pretends to be a C-level executive and asks someone to purchase gift cards for them. But BEC scams are getting far more sophisticated than this, making them much harder to identify. I will run through a few of these here so you have an idea of what to look out for and why you should always be sceptical in your daily work and communications.
Need for confidentiality
One of the primary ways BEC scams are foiled is through communication between personnel. To reduce the risk of falling victim to these scams, if you receive a communication that seems off, or asks you to buy something or transfer money, contact the requester. Use some other means apart from email to contact them, such as a phone call, or walk over to their desk and confirm its legitimacy. This is a critical measure in reducing the risks associated with BEC scams.
In more advanced BEC attacks, the first thing the threat actor tries to do is stop you from following this critical process making their attack more likely to succeed. A very common scenario we are seeing, within the very first contact email, the threat actor sets up a need for strict confidentiality. This is to reduce the likelihood that the recipient will go to their manager or someone else to confirm legitimacy. One scenario leveraged by threat actors is where the initial email, seemingly originating from the CEO of the company, informs the recipient about an ongoing acquisition of a new company. The email emphasises the importance of confidentiality due to financial market regulations and the risk of insider trading. This sounds like a valid request and reason for secrecy, and it reduces the risk of the recipient verifying the validity of the request.
No matter who the requestor is and their seniority, you need to check the request. Even in the above scenario, you can reach out to the CEO directly via phone and confirm without breaking the need for confidentiality.
Email display name spoofing
While many BEC scams use compromised email accounts because advanced BEC scams generally require impersonating specific people within an organisation and gaining access to these accounts may not be feasible, threat actors rely heavily on email spoofing instead and specifically display name spoofing.
Depending on your email client and your layout, when you receive an email, you see the sender’s name and possibly only their name. This is more prevalent on mobile devices where screen real estate is at a minimum. Threat actors set up email accounts specifically for their attacks using the name of the person they want to impersonate, hence spoofing the display name. If your CEO’s name is Eugene Belford, all you would see in the from field is “Eugene Belford“. Behind that name could be any email address. On a desktop mail client, usually you are afforded a longer view and would see the name in the format “Eugene Belford <ebelford@attacker.com>” and you would be less likely to fall for it. This is where threat actors will leverage the typosquatting techniques I alluded to earlier to reduce the risk of the victim identifying it as a fake email. Another method is to use the full format of “Eugene Belford <ebelford@emc.com>” as the sender’s name in the hope of compacted views looking even more legitimate or confusing the recipient in expanded views.
Multiple fake personas
Another key method threat actors are employing to legitimise BEC scams is the use of multiple fake personas, so basically including multiple people within the scam. This adds even more credibility to the attack. Going back to our example where the CEO requested help in a company acquisition, within this scenario, the original recipient is passed on to legal counsel in another company that specialises in acquisitions. This takes the recipient further away from the real CEO and the other personnel within their organisation which reduces the risk of the recipient getting wind of the scam. At this stage, a fake solicitor pretending to be from a well-known professional services or consulting firm is often used, leveraging their known email signature formats and logos, again building further legitimacy.
In other scams, initial emails are sent that contain complex email chain history. By creating a fake email chain, when the recipient receives their first correspondence, it appears long internal discussions have already been underway, and reading through these past emails again builds realism and legitimacy.
Building these types of email chains, as you can imagine, would be very time-consuming, and you would be right…. a year ago. With the advent of AI and easy access to tools such as ChatGPT, generating these types of email ‘conversations’ is extremely easy and fast. Feeding relevant names and information to generate a very legitimate-looking conversation is very easy to accomplish. For threat actors where this is their full-time job, it would not take much work to automate the development of these conversations leveraging AI tool APIs.
Use of Phone Calls
One final area to discuss is the use of phone calls in the later stages of these advanced attacks. Using email is a risk, a big risk for the threat actor. With advances in email security, along with difficulties in spoofing emails and other tell-tail signs of fraudulent activity, each additional email correspondence comes with the risk of being caught out. Email also leaves a paper trail of evidence that can be used during an investigation. Moving to a voice call makes logical sense to reduce this risk and they are often performed over channels such as WhatsApp or other free and less traceable services.
As you can imagine, the majority of threat actors reside overseas so strong accents are one sign to be aware of in these scams. But bear in mind we live in a very multicultural society, so someone with an accent isn’t anything out of the norm in our daily dealings. Again, AI has changed this dramatically as it is now quite simple to change your voice to another, in real-time. Connor has been doing some work on this for Morrisec and will be releasing a video on their Mos & Boo channel soon showing you how easy, and highly effective, this technique has now become.
How to defend against BEC scams
I have only scratched the surface of the various tactics used by threat actors when launching business email compromise attacks, techniques and tactics are evolving all the time. As we come up with new ways to thwart threat actor attempts, they come up with new ways to get by our controls. This is the continual cat-and-mouse game we play in the cybersecurity world.
So how do you defend against current and emerging BEC attacks?
- Security awareness training: For any attacks targeting personnel, the number one control is always security awareness training. I’m not saying this because it’s one of Morrisec’s primary services, it’s because threat actors target people as the weakest link in your defences. BEC scams are a perfect example of this, where traditional security measures have difficulty in stopping these attacks, so it’s 100% on the person receiving that initial correspondence. Those personnel need to have the knowledge and the skills to know what to look for so they don’t fall victim.
- Defined processes for financial transactions: We perform a lot of risk assessments and I’m happy to say I’m seeing more and more of this in place. For those employees that deal with any financial transactions, including performing tasks like updating payment details for customers or third parties, ensure you have processes in place to check the validity of those requests. And this should include verbal confirmation as you cannot rely on the safety of email. When performing bank transactions, having a secondary approver on the transaction limits this risk even further.
- External email flagging: Most present-day email systems have the ability to be configured to flag messages sent from external parties. You will see a small warning at the top of your email stating that the email is from an outside sender. If you received that email from the CEO and it’s flagged as from outside, it makes it very easy to spot that it is fraudulent. Internal emails from employees in your organisation will never be flagged.
- Implement email security protocols: One for the IT department and way beyond the scope of this article, but ensure Domain-Based Message Authentication, Reporting and Conformance (DMARC), Send Policy Framework (SPF) and Domain Keys Identified Message (DKIM) have been implemented. These will reduce the risk of fraudulent emails.
Finally, as mentioned previously, traditional security controls are unlikely to intercept initial attacks due to the use of legitimate domains and emails being devoid of suspicious links or malicious attachments. We are now seeing behavioural AI leveraged within email security that will hopefully help identify these types of emails and reduce the risk. In Gartner’s February 2023 Market Guide for Email Security report, they stated:
“Use email security solutions that include anti-phishing technology for targeted BEC protection that use AI to detect communication patterns and conversation-style anomalies, as well as computer vision for inspecting suspect URLs. Select products that can provide strong supply chain and AI-driven contact chain analysis for deeper inspection and can detect socially engineered, impersonated, or BEC attacks.”




0 Comments